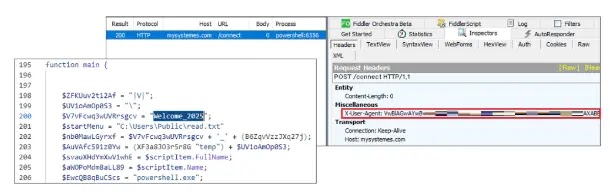
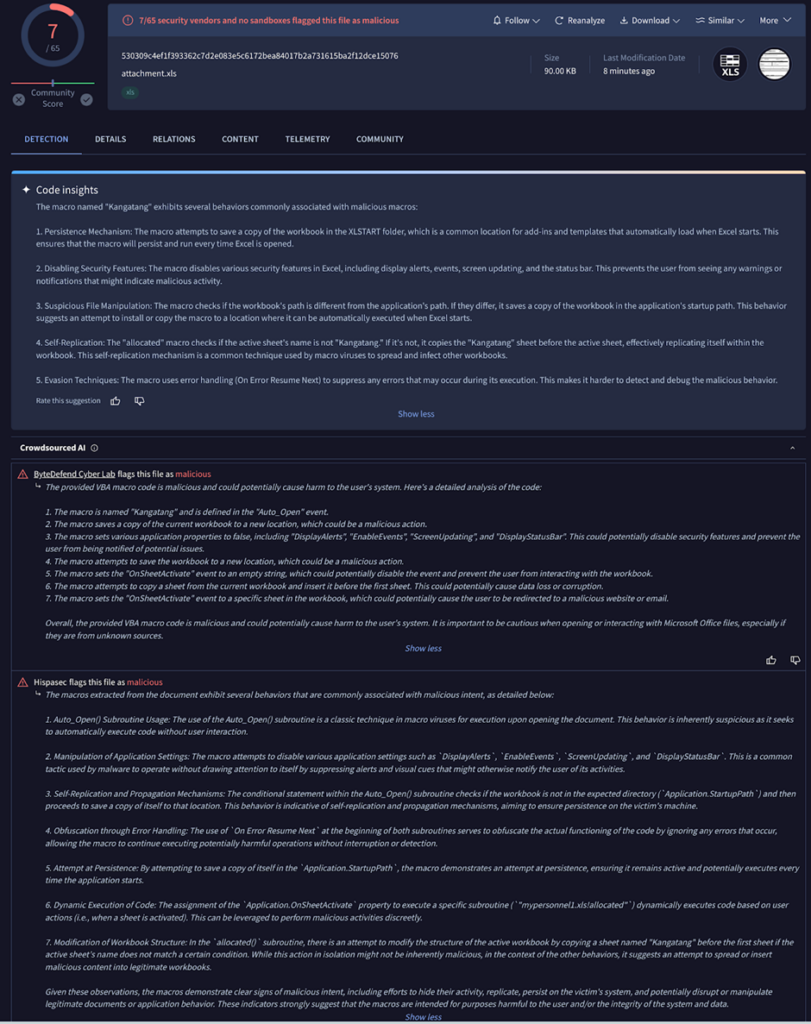
Hackers Exploiting Docusign With Phishing Attack To Steal Credentials
Hackers prefer phishing as it exploits human vulnerabilities rather than technical flaws which make it a highly effective and low-cost attack method. Phishing attacks can be easily scaled to target a large number of individuals, increasing the likelihood of success. Recently, cybersecurity analysts at Abnormal Security discovered that hackers are actively exploiting DocuSign with customizable … Read more


.webp)
.webp)

%20(1)%20(1).webp)
.webp)




.webp)