Addressing the Menace of Malicious Websites in Google Analytics
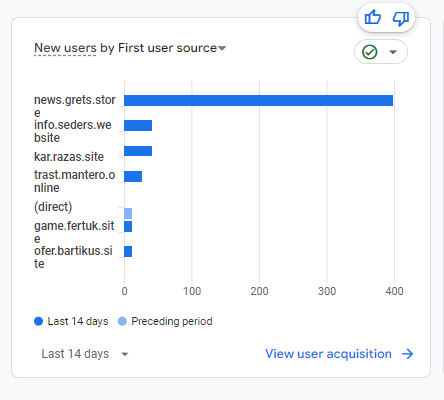
In today’s digital landscape, the presence of malicious websites in Google Analytics has emerged as a concerning issue, impacting the integrity of website traffic data and potentially posing serious security risks. This stealthy phenomenon can manifest through the infiltration of spammy referrals and nefarious bots, leading to skewed analytics reports and sabotaging the online presence … Read more





:format(webp)/cdn.vox-cdn.com/uploads/chorus_image/image/72651503/AP23256848600183.0.jpg)




