New Linux Backdoor Attacking Linux Users Via Installation Packages
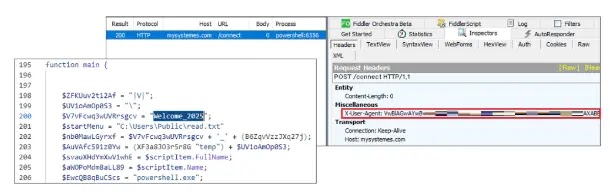
Linux is widely used in numerous servers, cloud infrastructure, and Internet of Things devices, which makes it an attractive target for gaining unauthorized access or spreading malware. Besides this, its open-source nature allows threat actors to study the code and identify new vulnerabilities in it closely. Cybersecurity researchers at Symantec recently identified a new Linux … Read more


%20(1)%20(1).webp)
.webp)